The AI Edge in Legal Reviews
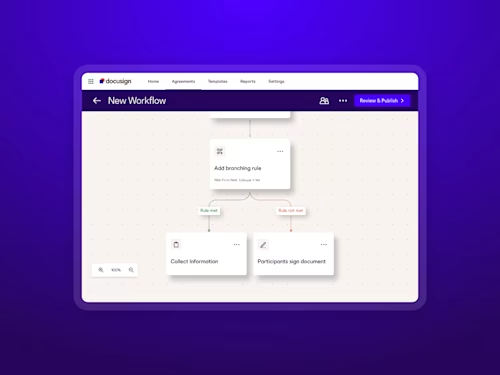
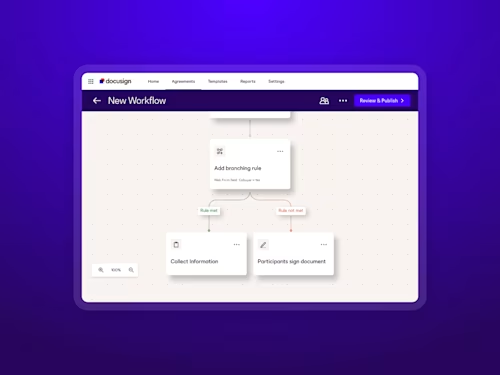
With multiple brands under one umbrella and a small in-house team, efficiency is a must at Steve Madden. Docusign AI-Assisted Review became a valuable tool for their team, enabling them to handle a 30% spike in contract volume—without expanding headcount or compromising accuracy.