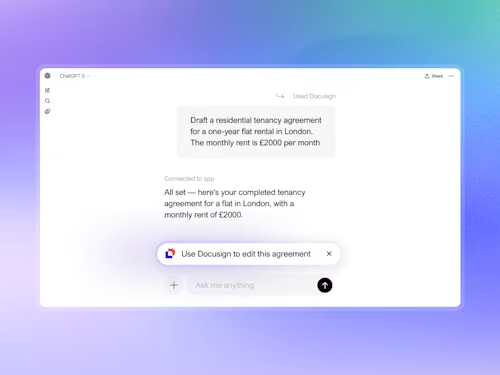
For AI to truly unlock value in contract management, a platform must go beyond basic document analysis. It needs to be trained on a rich, diverse, and consented contract datasets, integrate seamlessly with systems of work, and deliver enterprise-grade security, scalability, and trust.