Docusign Customer Awards 2025: Celebrating Innovation and Outstanding Achievements


Google is making security improvements in Chrome: beginning with release 80, Chrome will block insecure SameSite cookies set to None by default. These changes are being rolled out in multiple phases. The most important milestones are:
Chrome 80 Stable version release: 04-Feb-2020
Change in default settings of cookies: 17-Feb-2020
NaN. Cookies default to SameSite = Lax NaN. Reject insecure cookies when SameSite = None
This will impact any application that relies on cookies to store and track user sessions and is embedded and used on web pages hosted on different domains. Docusign is aware of this issue and is currently working to have fixes in place for all Docusign-owned products prior to widespread implementation.
If customer choose to opt into the new SameSite cookie settings in Chrome 80 prior to February 17, they may encounter the following errors:
Blank page sections show up while navigating to a page with embedded sending or signing.
Blank pages load with the error message, "XXX refused to connect."
Attempts to login fail and the user is redirected to the Login/Logout page.
Error pages load with the error message, "Bad request."
Integrations load incorrect pages in fragments (such as Home instead of Tagger).
If this change has impacted your organization, you can revert Chrome back to the previous behavior until you are able to bring your applications into compliance.
Warning: These are security-related settings. Work with your IT organization to review any changes made to Chrome flags prior to applying them in your Production environment.
Open Chrome settings by going to a new tab or window and typing: chrome://flags/
Search for SameSite flags by typing in the search bar.
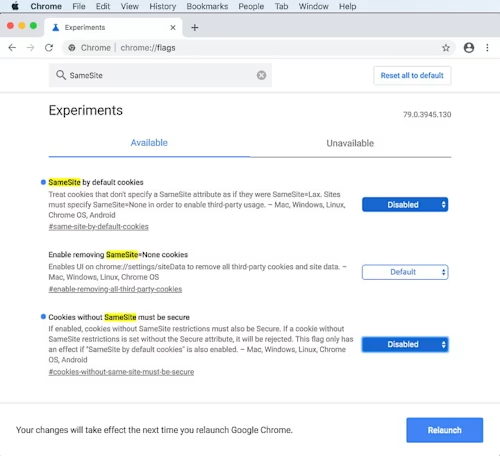
Set the settings to Disabled for the two settings shown in the screenshot below:
SameSite by default cookies
Cookies without SameSite must be secure
Relaunch Chrome.
Integrations need to make the following changes to any cookies:
Add attribute SameSite=None
Some older browsers, like Chrome 66 or before, and Safari on MacOS 10.14 or iOS 12 do not support the SameSite attribute and reject the cookies that have this attribute. So, an application needs to check for older browser versions and not send the SameSite attribute if detected.
Add attribute Secure
Any application that embeds third-party services in an iframe needs to check that the third-party services are sending the SameSite and Secure attributes correctly.

Related posts
